http://thommck.wordpress.com/2011/12/02/how-to-allow-non-admins-to-start-and-stop-system-services/
Any Microsoft Windows operating system has services. These are little programs that run in the background of the OS to keep things ticking over. They’re really fundamental to servers as it means that programs can run in the background without any user being logged. In fact Windows servers are fine-tuned to give better performance to background services rather than any app running on the screen.
It’s always the best principle to log on with the least amount of privileges on any PC, i.e. you shouldn’t log on to a desktop or server with full admin rights. You should log on as a normal user and only elevate the programmes authority to admin level if absolutely necessary.
Some System Administrators may want an easy life and just let everything “run as admin” as it cuts back on a lot of problems, especially when using old software. Obviously this greatly widens the security attack vector, as any user who can gain access to the machine can do anything they want on it.
However, one of the issues of running as a standard user is that you are not allowed to stop or start Windows services. That is by design, you wouldn’t really want a non-admin to stop a critical service. The problem is when you have a Service Account running (as good practice dictates) as a lowly user. To get around this you can give the Service Account permission to do whatever you want to a particular service you want. Unfortunately, this is a bit more convoluted than setting file permissions. This article will explain how to achieve this. It applies to all versions of Windows from Windows 2000 or newer. My screenshots are from the Windows 8 Developer Preview.
Scenario
A server on our network runs some aging but critical telephony software. The services run under a Service Account with a username of Svc-Phones. The Svc-Phones account also logs on to the server interactively to view any messages from the application or stop & start the services if there is an issue (avoiding a whole server reboot). The IT manager wants the Svc-Phones account to be removed from the local Administrators group to help secure the server. This means we will need to change the security permissions for the telephony program’s service.
Step 1 – Create the Console
We need to open a hidden console snap-in
- Click Start > Run (or press WIN + R) and type “mmc.exe”
- This opens an empty Microsoft Management Console. Click File > Add/Remove Snap-in… (Ctrl+ M)
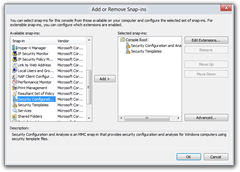 Scroll down the list of available Snap-ins and selectSecurity Configuration and Analysis
Scroll down the list of available Snap-ins and selectSecurity Configuration and Analysis- Click Add
- Next select Security Templates
- Click Add
- Click OK
Step 2 – Create a blank Security Template
In Windows Server 2003 and below you can store these files anywhere but later versions have tougher restrictions so we will be creating everything in D:\Securtiy\
- Right-click Security Templates from the console tree and select New Template Search Path …
- Browse to D:\Security, or other local path, and click OK
- Right-click D:\Security from the console tree and select New Template …
![Console1 - [Console RootSecurity TemplatesDSecurity] Console1 - [Console RootSecurity TemplatesDSecurity]](http://thommck.files.wordpress.com/2011/12/console1-console-rootsecurity-templatesdsecurity_thumb.png?w=240&h=108) Give the new template a name, e.g. Custom Services. It doesn’t matter what you use.
Give the new template a name, e.g. Custom Services. It doesn’t matter what you use.- The Description is optional but may be useful if you want to re-use it
- Click OK and you will see the new template appear in the console
The point of these templates are to lock-down servers using the Windows Security Configuration Wizard but we are only using them for a simple permission change
Step 3 – Create a Security Database
- Right-click Security Configuration and Analysis from the console tree and select Open Database…
- Browse to D:\Security, or other local path, and type a name in the File name: box e.gSecurity
- Click OK. This creates an Security.sdb file that is used to apply the changes
- An Import Template window appears. Browse to D:\Security/Custom Services.inf and selectOpen. This applies the template with all the local services to the database
- If you get the error “The database you are attempting to open does not exist.” then you need to choose a different path i.e. on a local disk
![Console1 - [Console RootSecurity Configuration and Analysis] Console1 - [Console RootSecurity Configuration and Analysis]](http://thommck.files.wordpress.com/2011/12/console1-console-rootsecurity-configuration-and-analysis_thumb.png?w=240&h=156) Right-click Security Configuration and Analysis from the console tree and select Analyze Computer …
Right-click Security Configuration and Analysis from the console tree and select Analyze Computer …- Click OK to accept the default log file path
- You will then be presented with something that looks very similar to the Group Policy Editor or Local Security Policy Console
Step 4 Change Service Permissions
 Double-Click System Services
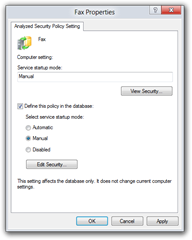
Double-Click System Services- Scroll down to find the service you need to change, e.g. Fax
- Double-Click the service
- Tick the box Define this policy in the database:
- Click the Edit Security … button
- Click Add
- Type in the user name of the Service account e.g. Svc-Phones, and click OK
- With the Svc-Phones account selected, check the Allowpermissions for Start, stop and pause
- Click OK
- Click OK on the Service Properties to bring you back to the console
![Console1 - [Console RootSecurity Configuration and AnalysisSystem Services] Console1 - [Console RootSecurity Configuration and AnalysisSystem Services]](http://thommck.files.wordpress.com/2011/12/console1-console-rootsecurity-configuration-and-analysissystem-services_thumb.png?w=240&h=128) You’ll notice the Service now has an ‘x’ on it and Investigate message on the Permission column. This is because the new permissions we’ve chosen conflict with what is on the local computer
You’ll notice the Service now has an ‘x’ on it and Investigate message on the Permission column. This is because the new permissions we’ve chosen conflict with what is on the local computer
Step 5 – Apply new Security Permissions
- Right-click Security Configuration and Analysis from the console tree and select Configure Computer …
- Click OK to accept the default log file path
- This will apply the new custom permissions to the local computer
- You can now test it out on the server with the Svc-Phones account and test it works
You can see that this is rather long-winded just to configure permissions on a service. thankfully, you can save everything and it will be quick to re-use in the future or as part of a batch process across servers. If you want to change the permissions on a default Microsoft Service you can use the Security section of Group Policy to achieve the same results
Related Reading:
- Microsoft Support article: How to grant users rights to manage services in Windows Server 2003
No comments:
Post a Comment